How to install and use TCPflow (TCPDump alternative)
On Unix-like systems like Linux, TCPflow is a free, open-source, and potent command line utility for network traffic analysis. It records information sent or received across TCP connections and saves it in a file for subsequent examination in a way that makes protocol analysis and debugging possible.
Since it processes packets from the wire or a saved file, t is a program similar to tcpdump. It is compatible with the same potent filtering expressions as its sibling. The sole distinction is that tcpflow organizes all TCP packets into separate files (one for each direction of flow) and assembles each flow for later analysis.
Its feature set also includes a sophisticated plug-in system for reversing MIME encoding, decompressing HTTP connections that have been compressed, and calling external programs for post-processing, among other things.
Tcpflow has a wide range of applications, including understanding network packet flows, forensics, and disclosing the contents of HTTP connections.
How to Install TCPflow in Linux
TCPflow can be installed using your package manager as described. It is accessible in the official repositories of many GNU/Linux distributions.
Install TCPflow in Debian/Ubuntu
sudo apt install tcpflow Install TCPflow in CentOS/RHEL
sudo yum install tcpflow Install TCPflow in Fedora 22+
sudo dnf install tcpflow TCPflow Options
Syntax: tcpflow [options] [expression] [host]-b: max number of bytes per flow to save -c: console print only (do not create files) -C: console print only, but without the display of source/dest header -d: debug level; default is 1 -e: output each flow in alternating colors(Blue=client to server;Red=server to client;Green=Unknown) -f: maximum number of file descriptors to use -h: print this help message -i: network interface on which to listen -p: don’t use promiscuous mode -r: read packets from tcpdump output file -s: strip non-printable characters (change to ‘.’) -v: verbose operation equivalent to -d 10
You can execute tcpflow with superuser permissions after installation; otherwise, use the sudo command. Remember that it is listening on the current network interface (for instance, enp0s3).
sudo tcpflow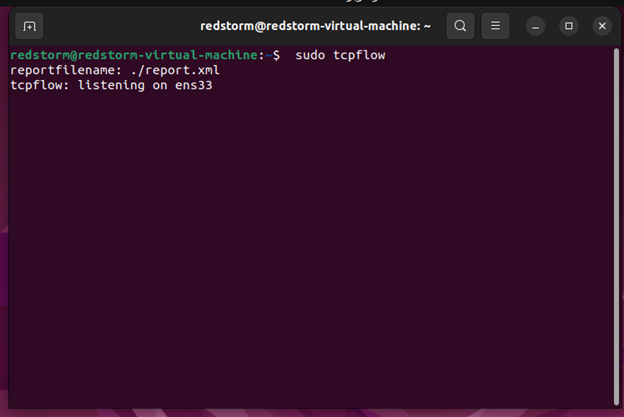
By default, tcpflow stores all recorded information in files with names that begin with (this may be different if you use certain options such as a timestamp).
Transcript files are, by default, kept in the current directory by tcpflow. You can select the output directory where the transcript files will be written with the -o option.
sudo tcpflow -o tcpflow_files sudo ls -l tcpflow_files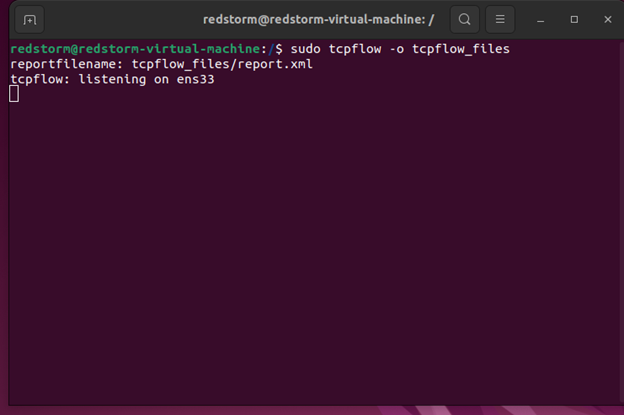
The -c flag can be used to print the contents of packets to stdout as they are received without saving any captured data to files. Open a second terminal, perform a ping, or surf the internet to test this effectively. You ought to be able to see the ping details or the surfing details that tcpflow is collecting. sudo tcpflow -c It is possible to record all activity on a certain port, such as port 80. (HTTP). When dealing with HTTP traffic, you can view the HTTP Headers, followed by the content, on stdout or in a single file if the -c flag is not present. sudo tcpflow port 80
Use the -i flag to specify the name of the network interface you want to capture packets from.
sudo tcpflow -i eth0 port 80The -a flag, which is the same as the -e all option, enables all processing utilizing all scanners.
sudo tcpflow -a OR
sudo tcpflow -e allAdditionally, a specific scanner can be activated; the available scanners include md5, http, netviz, tcpdemux, and wifiviz (run tcpflow -H to view detailed information about each scanner).
sudo tcpflow -e httpOR
sudo tcpflow -e md5OR
sudo tcpflow -e netvizOR
sudo tcpflow -e tcpdemuxOR
sudo tcpflow -e wifivizThe example that follows demonstrates how to enable all scanners other than tcpdemux.
sudo tcpflow -a -x tcpdemuxBefore capturing packets, TCPflow often tries to enter promiscuous mode on the network interface. By setting the -p flag as shown, you can stop this.
sudo tcpflow -p -i eth0Use the -r flag to read packets from a tcpdump pcap file.
sudo tcpflow -f file.pcapVerbose mode can be enabled using the -v or -d 10 options.
sudo tcpflow -vOR
sudo tcpflow -d 10The inability of tcpflow to currently comprehend IP fragments means that data transmitted as part of TCP connections that contain IP fragments will not be correctly collected.
Consult the tcpflow man page for more details and available usage options.
man tcpflowConclusion
A TCP/IP demultiplexer is tcpflow. Tcpflow is used to monitor thousands of connections, but it is most often used to capture traffic between two servers. By actually capturing the real data and dumping it into a file we choose, Tcpflow distinguishes itself from other programs.
It can then be applied to other types of analysis. Tcpflow has the additional benefit of successfully reconstructing damaged packets. Tcpflow offers a wide range of filter choices as well. There are several various methods we may use to quickly filter the capture out.
Arp poisoning typically constitutes the initial step of the majority of sniffing assaults. Tcpflow, on the other hand, catches practically all data without purposefully contaminating the subnet or network.
FAQ
How does TCPflow's performance compare to TCPDump in terms of resource usage and speed, especially when handling high volumes of network traffic?
TCPflow is generally considered to be efficient in handling network traffic, similar to TCPDump. However, its performance advantage might come from its ability to reconstruct the actual data streams from captured packets, potentially offering a more intuitive analysis experience, especially for high volume traffic.
Can TCPflow be integrated with other network analysis tools or platforms, and if so, how?
TCPflow can often be used in conjunction with other network analysis tools through its output files. The data captured and processed by TCPflow can be further analyzed or visualized using specialized software designed for network diagnostics or security analysis.
Are there any known compatibility issues or limitations when using TCPflow on different operating systems or environments not covered in the installation guide?
TCPflow is designed to be cross-platform, with support for various Unix-like operating systems, including Linux and macOS. However, its performance or compatibility may vary based on the system architecture, version, and the presence of required libraries. Detailed compatibility issues or limitations specific to different environments would typically be documented in the official documentation or community forums.