Introduction
The ipconfig command updates DHCP and DNS settings and displays details about your network configuration. The ipconfig command by default shows the default gateway, subnet mask, and IP address. However, you may extract much more information from it with the right parameters.
The ipconfig command and its various options will be explained in this article.
How to Open Command Prompt
You must open the Command Prompt window in order to use this tool. The Command Prompt window can be opened in one of three ways:
- Use the Windows search feature to look for “cmd.”
- Right-click the Start button and choose Command Prompt.
- Press WinKey + R on your keyboard, and then type cmd in the Run window.
How to use the ipconfig command
So, let us start with something easy, like how to use the ipconfig command.
After CMD is opened. Type:
ipconfigThis will show you the most basic information about your network from your network adapters.
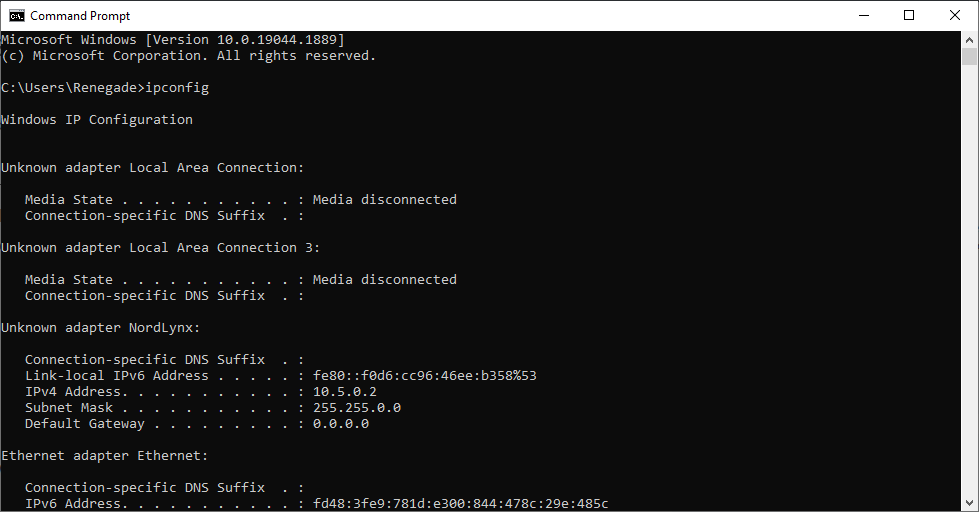
As you can see from the above screenshot, the Command will tell you about each network adapter on your computer. In this case, we have a wired (ethernet) network adapter and a wireless (Wi-Fi) network adapter. If you have a VPN client, it will also show up as a network adapter.
all Option
The Command displays only the most basic network information without using any parameters. But by default, no information on the DNS and DHCP servers is shown. You must use the /all argument to display all the details about your network adapter.
ipconfig /allThe following details will be returned for each network adapter in your device:
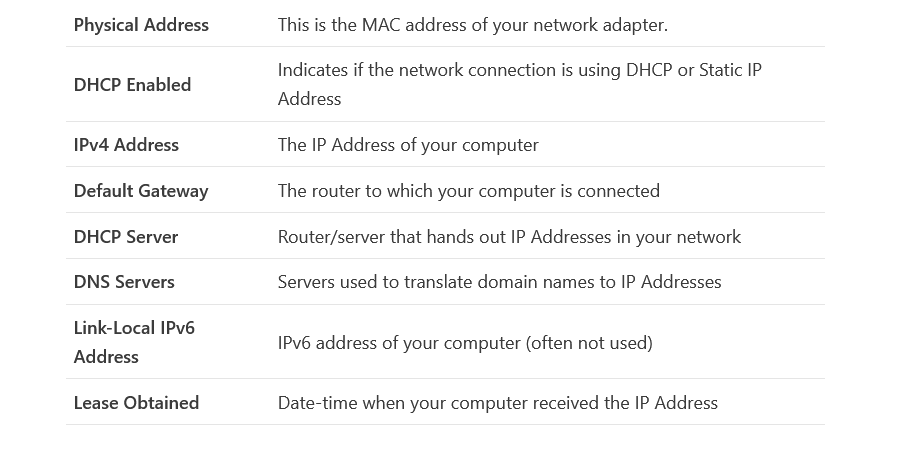
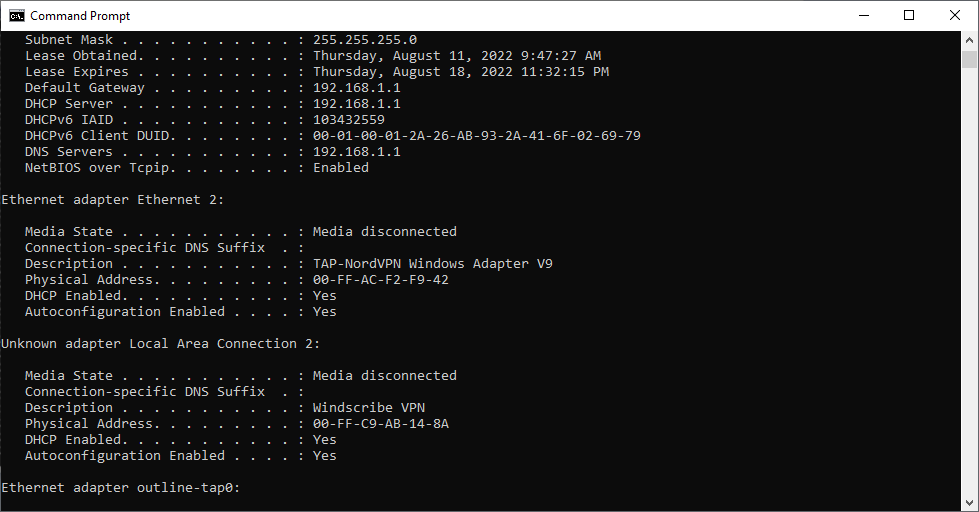
The ipconfig /all tool is frequently used to diagnose issues with network connections.
release Option
The ipconfig command can reset or update your network settings and display information about your configuration. You can ask the DHCP server for a new IP address if DHCP is enabled on your network card.
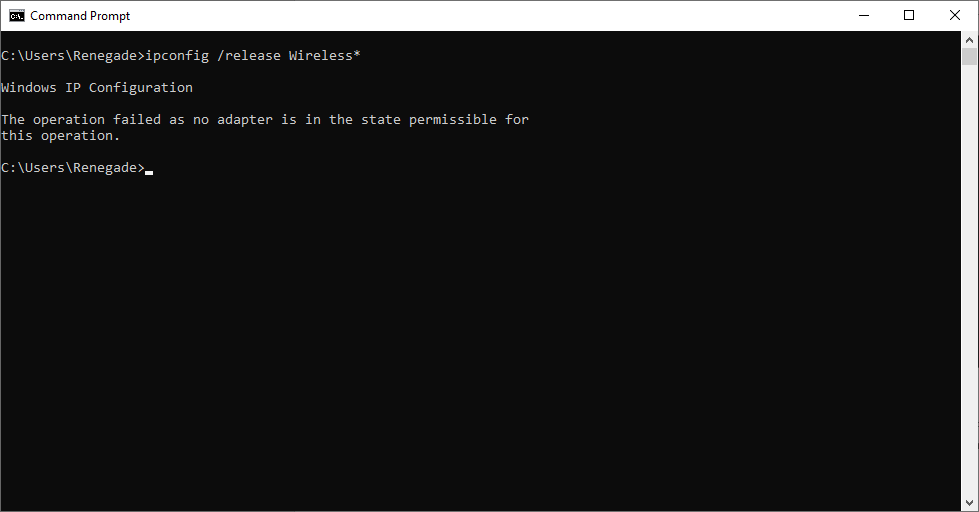
To start, the current IP address must be made public. Doing this will let the DHCP server know that we no longer want to use the provided IP Address.
ipconfig /release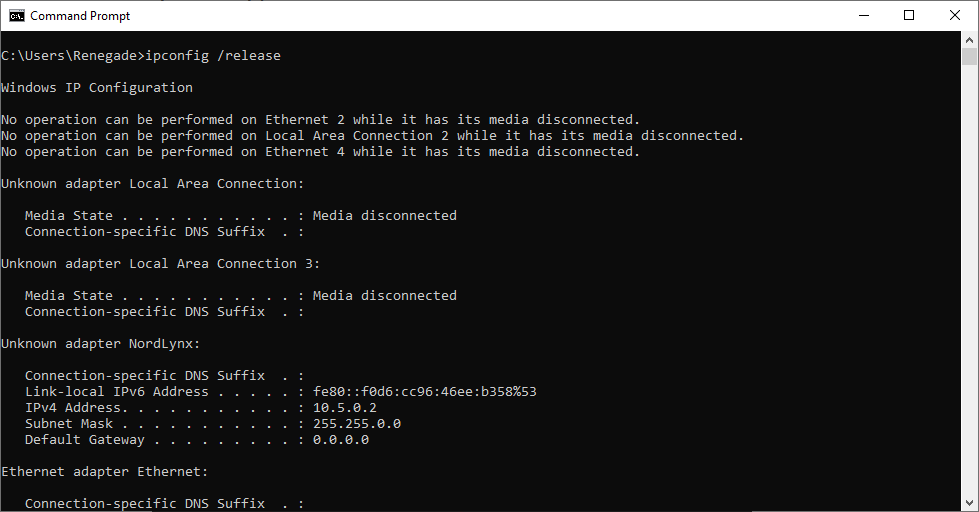
The Command will, by default, release the IP addresses for every network interface. Additionally, a single network adapter may be specified. It would help if you input the name of the adapter that you see here in the output of ipconfig in order to accomplish this:
ipconfig /release Wireless*renew Option
After releasing an IP Address, a new one must be requested from the DHCP server. This is possible using the Ipconfig /renew Command:
ipconfig /renewIf the renewal was successful, you would receive the same output as the ipconfig command, which includes an overview of your new IP Address, subnet mask, and gateway.
Once more, we can specify a single network adapter by providing the adapter’s name.
ipconfig /renew Wireless*Display DNS Command
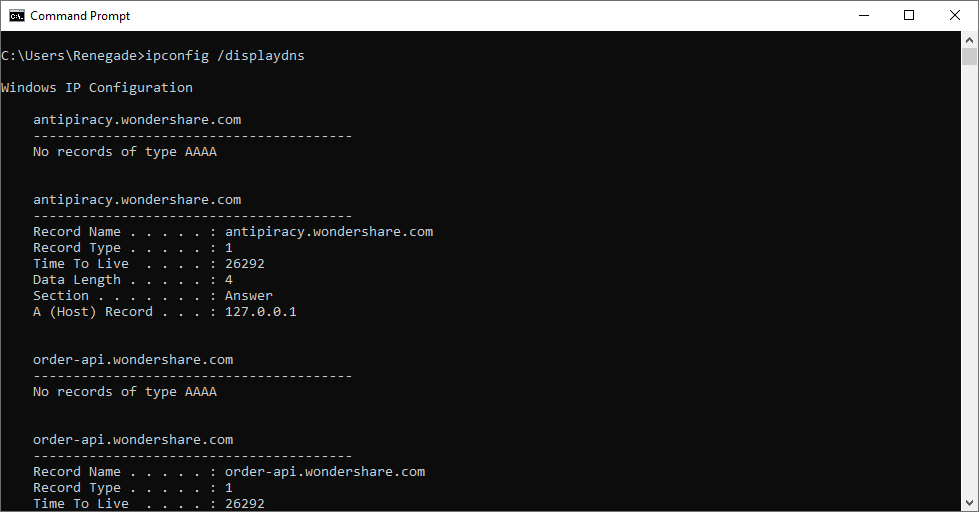
Your computer maintains a local cache of all visited DNS records. This cache quickly translates domain names to their corresponding IP addresses. This eliminates the need for your computer to contact the DNS server each time you visit Google.com, for example:
You can perform the command ipconfig /displaydns to view the DNS cache’s contents.
This will display each DNS record in the DNS cache:
ipconfig /displaydnsFlush DNS Command
Occasionally, your DNS Cache may contain obsolete records, resulting in DNS-related errors (unable to reach websites, for example). Typically, this can be resolved by executing the flush DNS Command.
ipconfig /flushdnsThe ipconfig /flushdns command clears your DNS Cache. This is risk-free; your computer will simply request updated DNS records from the DNS servers.
Monitor your Windows Server using Xitoring for free!